RedTeam Exercises with OpenSource Tools part 1
Can RedTeam exercises be done today by only using open source tools?
Do they have 100% yield or success?
Can I compete with the top solutions in a RedTeam vs BlueTeam engagement, BlackBox or WhiteBox exercise, using only open source tools and having the same result as the enterprise solutions like: Canvas, Metasploit Pro, Open Core, Cobaltstrike?
In the next articles, I will approach proper ways to compete with the top security researchers from the companies focused on security products, and how to combine or customize multiple open source solutions for achieving the same result.
Contents
- Short Introduction
- What is AMSI?
- How do I make use of opensource
- Code Obfuscation
- Invoke Obfuscation
Introduction
I have chosen to focus on how we can compromise a Windows based system up to date (11.04.2020 - the date I am writing this article) having all the security modules enabled, mostly because it is less probable to encounter a Linux based system with a security solution in an enterprise environment.
We can see a number of measures implemented in Microsoft’s operating system that have no role other than to provide a greater protection system for user’s experience:
- Windows Defender
- Antimalware Scan Interface (AMSI)
- Control flow guard
- Data Execution Prevention (DEP)
- Randomized memory allocations
- Arbitrary Code guard (ACG)
- Block child processes
- Simulated Execution (SimExec)
- Valid stack integrity (StackPivot)
I will not advertise Microsoft products but as I focus on proving that we can still bypass their solutions, I can not say that they didn’t do a good job regarding thier security solutions (maybe they are intending to sell security services like many others if they haven’t started already). There is one security solution from Microsoft that I encountered more than I intended to, and I burned my arsenal in development or pentests before finding out what stopped me and why. I am pretty sure you encountered it too even if Windows Defender was not the main AV/AntiMalware solution from your target. I think you what I am talking about :).
What is AMSI?
As you guessed, I was referring to AMSI; before focusing on how to make use of the open source tools for a RedTeam exercise, we have to bypass Microsoft’s security modules, this meaning we have to bypass AMSI too. Before reviewing the methods of bypassing AMSI, we need to clarify a little about what AMSI is, under what principles AMSI works and how it has the ability to catch even the most exotic payloads.
AMSI is an interface that allows to the OS’s applications and services to integrate with any antimalware product that’s present on a machine. It supports a calling structure allowing for a file and memoy or stream scanning, content source URL/IP reputation checks and other techniques. It also supports the notion of a session so different antimalware vendors can correlate different scan requests, this being pretty bad for our stagers if they are catched by AMSI.
As we can see in the above image, AMSI is integrated by default in the Windows’ components meaning that, for example, we have a powershell script containing some commands; those commands will be analyzed based on some string patterns and in case they match, then Windows Defender/ Microsoft’s Sandbox will start as follows:
- User Account Control, or UAC (elevation of EXE, COM, MSI, or ActiveX installation)
- PowerShell (scripts, interactive use, and dynamic code evaluation)
- Windows Script Host (wscript.exe and cscript.exe)
- JavaScript and VBScript
- Office VBA macros
As things were not enough bad, Microsoft improve the logging capabilities of Windows Defender so we have the risk to alarm the whole network of our presence if there is a SOC team.
> Get-WinEvent ‘Microsoft-Windows-Windows Defender/Operational’ -MaxEvents 1 | Where-Object Id -eq 1116 | format-listAs we can see Windows Defender already logged our activity of trying to execute our payload in memory. As source of detection is menitoned AMSI. This can be easily automated in a SIEM to trigger an alert and all of our efforts of getting on the workstation would be useless.
AMSI may provide a result between 1 and 32767. The larger the result, the riskier it is to continue with the content. These values are provider specific, and may indicate a malware family or ID. Any return result equal to or larger than 32768 is considered malware, and the result is blocked. A list from Microsoft docs will explain each range of values what means:
- AMSI_RESULT_CLEAN - Known good. No detection found, and the result is likely not going to change after a future definition update.
- AMSI_RESULT_NOT_DETECTED - No detection found, but the result might change after a future definition update.
- AMSI_RESULT_BLOCKED_BY_ADMIN_START - Administrator policy blocked this content on this machine (beginning of range).
- AMSI_RESULT_BLOCKED_BY_ADMIN_END - Administrator policy blocked this content on this machine (end of range).
- AMSI_RESULT_DETECTED - Detection found. The content is considered malware and should be blocked.
According to Microsoft docs “results within the range of AMSI_RESULT_BLOCKED_BY_ADMIN_START and AMSI_RESULT_BLOCKED_BY_ADMIN_END values (inclusive) are officially blocked by the admin specified policy. In these cases, the script in question will be blocked from executing. The range is large to accommodate future additions in functionality”.
This looks bad until now but courage, there is hope :).
How do I make use of open source?
As a penetration tester, I have to prioritize what I want to complete first for having a prepared arsenal for any penetration test. Because time is precious to every one of us, we have to move fast:
- Get a working base code first from Empire, Metasploit, etc., would be ideally instead of reinventing the wheel (reinventing the wheel is a good thing if you are a malware developer - but this is a story for other article :) ).
- Customize functions - change default parameters/functions names, delete comments, write the functionality in other way, etc.
- Obfuscate code.
- Test against AV - Make sure you disable the option for permitting to Microsoft to upload your sample in their cloud sandbox. This will just waste your precious payload.
So this being said, i have chosen to go on the BC SECURITY’s solution, the reborn Empire (epic music should be played on at this phrase).
Why Empire and not other solution?
At this moment Empire is a robust and mature framework for post-exploitation, the guys from BC-Security really did a good job after they forked the official unsupported project. I personally, when it comes to chose a platform, i prefer a solution that can be easily used by my team mates/ eventually colaborate all together on it through an API/ web interface. Empire has both API and web interface for multiple user colaboration.
Few pros why i have chosen Empire and you should go for it too, in case you are the clasic guy who works with classic tools:
- Encrypted C2 channels and multiple protocols/services supported for communications.
- Adaptable modules: .bat, .vbs, .ddl, etc.
- Alot of evasion capabilities enabled by default.
Even if a lot of research articles are mention that powershell for redteams is no longer used by APTs as main tool of exploitation, i do not see their point. Powershell for redteams is a great tool if you are using it just for a legit pentest and nothing more:
- Operated in memory.
- Installed by default on Windows systems
- Full .NET access.
- Direct access to Win32 API.
- Admins typically leave it enabled.
Below is a scheme of how Empire stager is deployed.
Okay so we completed the first step. I have chosen a base code to use as our main tool of attack. However default Empire will get me caught. It can not pass the AMSI protection of Windows system so obfuscation or changes are needed.
Code Obfuscation
Because we have chosen powershell as our main programming language for malware developing, I will present few ways of how can we can obfuscate our code.
1.Randomized Capitalization
Powershell is ignoring capitalization. Every antivirus/antimalware solution is heavily dependent upon signatures, this including signatures based on hashes.
Even if AMSI is ignoring capitalization, changing the payload’s hash is a good practice.
2.Concatenation
AMSI is still heavily dependent upon signatures, however simple concatenation can prevent most alerts. Microsoft has implemented a custom EICAR string ‘amsicontext’ for testing the AMSI’s detection capabilities.
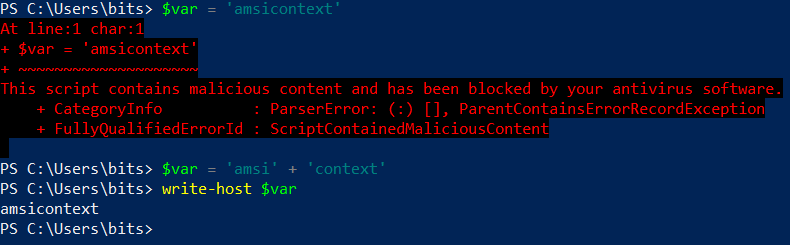
3.Variable Insertion
Powershell recognizes $ as a special character in a string and will fetch the associated variable.
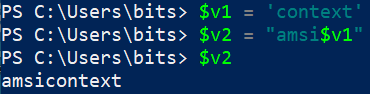
4.Format String
Powershell allows for the use of {} inside a string to allow for variable insertion. This is an reference to the format string function.
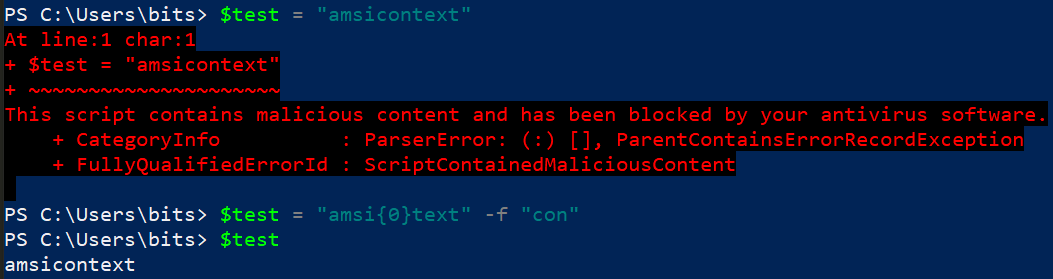
As you can see, AMSI is still not perfect in detecting all of above examples, maybe in time it will can. The list of obfuscation methods can continue from compressing the code to encrypting it, etc.
Also a good tip, is to break large section of code into smaller pieces and test them in part in order to determine what is being flagged in your stager when you develop the obfuscation.
However I promised that we will make use of multiple open source tools for achieving our goal and not losing to much time on development.
A script will come in play in our aid when it comes obfuscation, so lets Invoke-Obfuscation!
Invoke-Obfuscation
If you have not already viewed Daniel Bohannon’s presentations about Invoke-Obfuscation , I invite you to take a look at the following presentation1 or presentation2 .
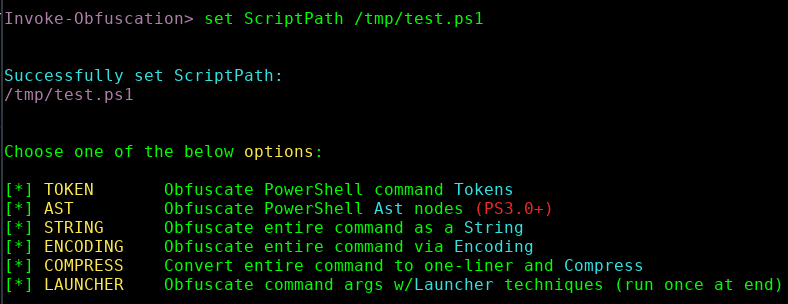
“ScriptPath” is setting the path for reading the content from a file, in my case will be “/tmp/test.ps1”, where test.ps1 is containing the following code:
Write-Host "I like WHmacmac's articles" -ForegroundColor BlueWithout entering in to many details about it, lets see a little about its obfuscation techniques:
1. Token obfuscation
The most used obfuscation method in our days is based on token, in special Empire is coming with Token/ALL obfuscation as default. If you chose to go for the Token/ALL, it will do a long set of changes like variable insertation, concatenation, comments removing, variable renaming, inserting random whitespace, etc. It is extremly useful for masking variable names to AMSI.
Example of output:
.("{0}{2}{1}" -f 'Wri','-Host','te') ("{3}{1}{2}{0}{4}"-f 'ti','voke-O','bfusca','In','on') -ForegroundColor ("{0}{1}"-f'Bl','ue')However beucase it was extremely used in the last years, this will get you caught. It is recommended to run whitespace last (at least 2-3 times).
2. Abstract Syntax Tree (AST) obfuscation
An AbstractSyntaxTree (‘AST’) is a commonly used structure to represent and parse source code in both compiled and interepreted languages. PowerShell is unique in that it exposes the AST structure in a way that is friendly to developers and is documented extensively .
AST at base can easily find language elements. It is breaking the structure of the code and it is linking structures of code; AMSI will look at each structure of code in part and the token obfuscation will not help us to bypass it because they will be reduced at the basic form. AST contains all parsed content in Powershell code without having to dive into text parsing (we want to hide from this).
The AST obfuscation method will change the structure of AST.
3. Encoding Obfuscation
It is used to mask the payload by converting the format in Hex, ASCI, Binary, AES encrypted, etc. Beware because Powershell interpreter has a limit of 8191 characters so carefull how much encoding you do. This will works fine with the compressing method in case you apply multiple encoding methods recursively.
Example of output encrypt the entire command as SecureString (AES):
& ((VaRIAble '*mdr*').nAmE[3,11,2]-JOIN'')( ([RUNTimE.intEropservIcEs.MARsHaL]::PTrtOStrInGAuTo([RUNtImE.iNteROPSERvIceS.mARShAL]::sEcuREsTRInGToBsTr( $('76492d1116743f0423413b16050a5345MgB8AEwAcgA2AHcAZgBZAGEAVgBrAEUAWQBmADYAUQBtAHMARABZAFoAbgBPAEEAPQA9AHwAOAAxADYAYQAxADgAZABlADEANAAwAGIAZQBkAGEAYwAwADkAMgAxAGYANQA0ADEAZABmADYAYgBmAGEAMgA3ADIAMQAxADIANgBiADIAYQBmAGIANwBmADkAZAA4ADgAYwAxADYAMwBkADEAYgAzADUAMwBkAGIANwAzADcANABhADAANgAxAGMANgAxADQAYQA0ADcANAAyAGUAMABlADcAMgA0ADkAYgAyAGQAYwBhADMAZgBhAGUAYQBhADUAYgA3ADcANAA2ADQAMABmADYANgAxADYAOQBlADkAMQAyAGIAMgBiADEAOAA1ADUANgBmAGIANQAxADEANgA0ADkAMQBkAGQAZQA3ADUAMAA1ADUAMgAxADEAZAAyADcAMgA3ADEAZgA2ADQAYwAxADkANAA1ADUAOQBkAGMAZQA5AGMANQBkADQAMwBkADUAZQA0AGUAYQA2ADkAMABlAGEAZAA1AGIAZABlAGMAOQBiADIAZQA4ADAANQA0ADEAMgA5ADcANwA4ADMAZABkAGYANAA4AGUAZAAxAGMAMwA4AGEAMwAyADUAYwAzADQAMQBlAGMAYgA2ADMAYQA5AA==' |CoNverttO-SecuRestRinG -keY (100..69)) ) ) )
4. String Obfuscation
Obfuscated Powershell code as a string.
Breaks up the code with reversing techniques and concatenation.
Example of output concatenating the entire command:
iNVOkE-EXPressION( (('Write-Host {'+'0'+'}'+'Inv'+'o'+'ke-O'+'bf'+'u'+'sca'+'tion{0}'+' -F'+'or'+'egroundC'+'o'+'lor '+'B'+'l'+'ue')-f [ChAR]34) )
5. Compress Obfuscation
Compress obfuscation can be used in conjunction with Encoding to reduce the overall size of the payload.
Example of output:
( new-oBjeCt SYStEm.IO.strEamReaDer(( new-oBjeCt SystEM.io.CompREsSIoN.DeFLAtestrEaM([SySTeM.iO.MEmorYSTREaM] [coNvert]::frOmbasE64StrING( 'Cy/KLEnV9cgvLlFQ8swry89O1fVPSistTk4syczPU1LQdcsvSk0vyi/NS3HOz8kvUnDKKU3lAgA=' ), [SYStEm.io.cOMprEssion.cOMprEssiONMoDe]::deCOMPrEsS ) ),[TeXt.eNCODiNG]::ASCii)).rEaDToEnd( ) |&( $pshOme[4]+$Pshome[30]+'X')
6. Obfuscate Command Args
Many pentesters are underestimated the Launcher obfuscation in their malware development phases. In the below image we can what methods of launcher obfuscation are available for us.
As we can see many of them are including “somethingbla IEX”. Microsoft learnt from the past and any input passed to the IEX command will be verified by the AMSI or Windows Defender. This can be problematic because it can ruin all of our obfuscation efforts. Below is a proof of AMSI detection of a malicious variable passed to IEX. I recommend using WMIC instead of IEX if it is possible.
Empire already includes a launcher based on IEX. At this moment the community/I do not know a replacement for IEX. Maybe there is but Microsoft did not document all of these little tricks because they do not wanna let the APTs to take advantage of it.
Example of output using wmic as launcher:
C:\wINdOws\sySTEm32\wBEm\WmIC prOcESS "call" 'CREAte' "POwErShElL Write-Host "\"Invoke-Obfuscation"\" -ForegroundColor Blue"
Conclusions
Empire has integrated Invoke Obfuscation in its stager’s console.
Mix them up to avoid detection.
Example:
- Token\String\1,2
- Whitespace\1
- Encoding\1
- Compress\1
Example of how to use multiple obfuscation methods in Empire:
set Obfuscate True
set ObfuscateCommand Token\String\1,1,2, Token\Variable\1, Token\Whitespace\1,1, Compress\1
In the next article, we will see how to apply all what we discussed to bypass Windows Defender, AMSI and get a reverse shell. We will approach few scenarios in what will follow.
Please let me know your feedback about it :).
References:
https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-antivirus/troubleshoot-windows-defender-antivirus
https://docs.microsoft.com/en-us/windows/win32/amsi/how-amsi-helps
https://docs.microsoft.com/en-us/windows/win32/api/amsi/ne-amsi-amsi_result
https://www.bc-security.org/post/the-empire-3-0-strikes-back
https://github.com/BC-SECURITY/Empire
https://docs.microsoft.com/en-us/windows/win32/api/amsi/
https://threatvector.cylance.com/en_us/home/how-to-implement-anti-malware-scanning-interface-provider.html
https://blog.rapid7.com/2018/05/03/hiding-metasploit-shellcode-to-evade-windows-defender/
https://www.cyberark.com/threat-research-blog/amsi-bypass-patching-technique/
https://www.youtube.com/watch?v=F_BvtXzH4a4
